Did you know that only 27.9% of the merchants surveyed in the 2020 Verizon Payment Security Report were able to maintain full PCI DSS Compliance in 2019? In fact, full compliance dropped from a high of 55.4% in 2016 by 27.5% in just 3 short years. Since 2010 when Verizon began publishing this report, Requirement 11 is the number one repeat offender of being the least compliant key requirement. More than anything, what the recent Verizon report shows is how challenging achieving, maintaining, and sustaining PCI DSS Compliance is for most merchants.
One of the biggest mistakes merchants make is not having processes in place for the PCI DSS requirements that have frequencies. Most merchants don’t even know they’re making this mistake until it’s time for their annual PCI Report on Compliance, and by then, it’s too late. They don’t have four quarters of internal vulnerability scans, ASV scans, proof of scans after significant change, etc.
We remember what it’s like – to be down in the weeds, chasing after system administrators who were oblivious to their PCI responsibilities and having the QSA point out obvious things we missed. We know what it’s like to have that call with the Acquirer, to explain what we missed, how we fixed it, and ask if they’d accept the risk of not having quarterly or worse, monthly evidence that proved we had the control in place.
We know what it’s like to not have a staff and to figure out how to wrangle a Fortune 100 company and level 1 merchant into PCI DSS Compliance effectively and efficiently.
Through our Ultimate Guide On How To Manage PCI DSS Requirement Frequencies, we’ll walk you through each requirement area and show you what the specific requirement frequencies are, why they have a frequency, and we’re going to share our best practices on how to create sustainable processes so that you can maintain PCI DSS Compliance without pulling your hair out.
Every other week beginning July 13, 2021, we’ll be breaking it down for you. Be sure to sign up for the Payment Card Assessments Blog and Newsletter so that you don’t miss a post.
Over the course of the next eight months, we’re going to show you how we implemented control frequency processes that not only automated notifications to system administrators to submit their evidence but also how we created dashboards to monitor key controls and reporting so that senior management had near real time information at their fingertips. The processes we implemented reduced churn, saved money, and made the QSA’s assessment job easier.
Our Planned Schedule For The Series:
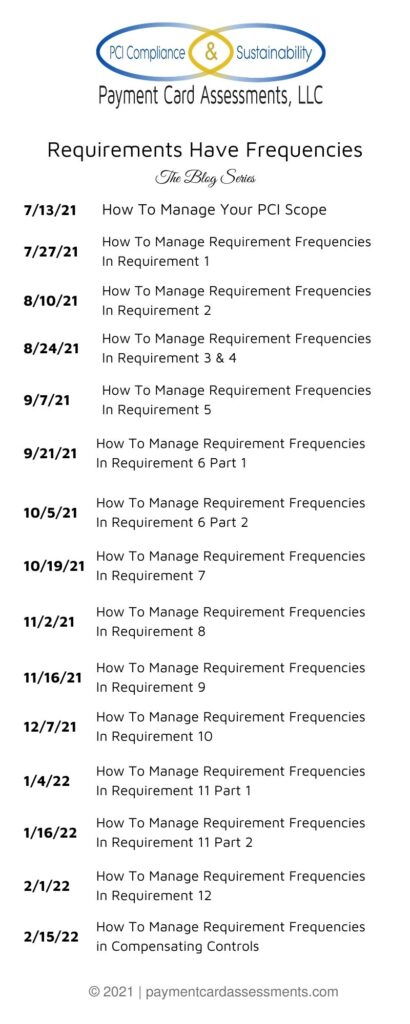

If your PCI DSS Compliance needs are more urgent than the timeline we’ve set for the our Ultimate Guide On How To Manage PCI DSS Requirement Frequencies, request a call back today. We’ll schedule a free 30 minute call to discuss your immediate needs and determine if partnering with Payment Card Assessments is the right fit for your company.
